Utilize have seen an increase in advanced Phishing Email Attacks
By Mark Risidore
20/09/2023
Utilize have seen an increase in advanced Phishing Email Attacks and CEO impersonation emails across our client base and in the Cyber Security Space.
Phishing Attacks
Attackers can now pay for AITM (Adversary Man in the Middle) services on the DarkWeb. Essentially this is a Service where, you can import targets email addresses and it will send them a specifically crafted email link. Once this link is clicked it will load a very genuine looking website, hoping the recipient will input their Office365 credentials. Simply put, this website acts as a middle proxy server sending your genuine credentials to Office365 services, then displaying an MFA prompt for the user to approve. If this is done, the attacker not only has your Office365 credentials, but also the MFA token to use for future use for 90 days. Until the token is revoked, and credentials changed the attacker can access everything you can in Office365!
This is why it’s imperative to not input any credentials or approve any MFA prompts unless:
1. You know it’s a genuine MFA prompt you are expecting
2. The website address is a genuine Office365 website
If you are ever unsure, pause what you are doing and log a ticket with the Utilize Service Desk who can confirm if genuine. Either by email: service@utilize.co.uk or telephone 0333 006 9060.
Attackers are investing more resources, time, and money in these attacks to try and fool targets. Most attacks rely unfortunately on social engineering, to try and trick the end user into believing a link or website is legitimate.
Let’s take a look at some examples we have seen in the ‘wild’.
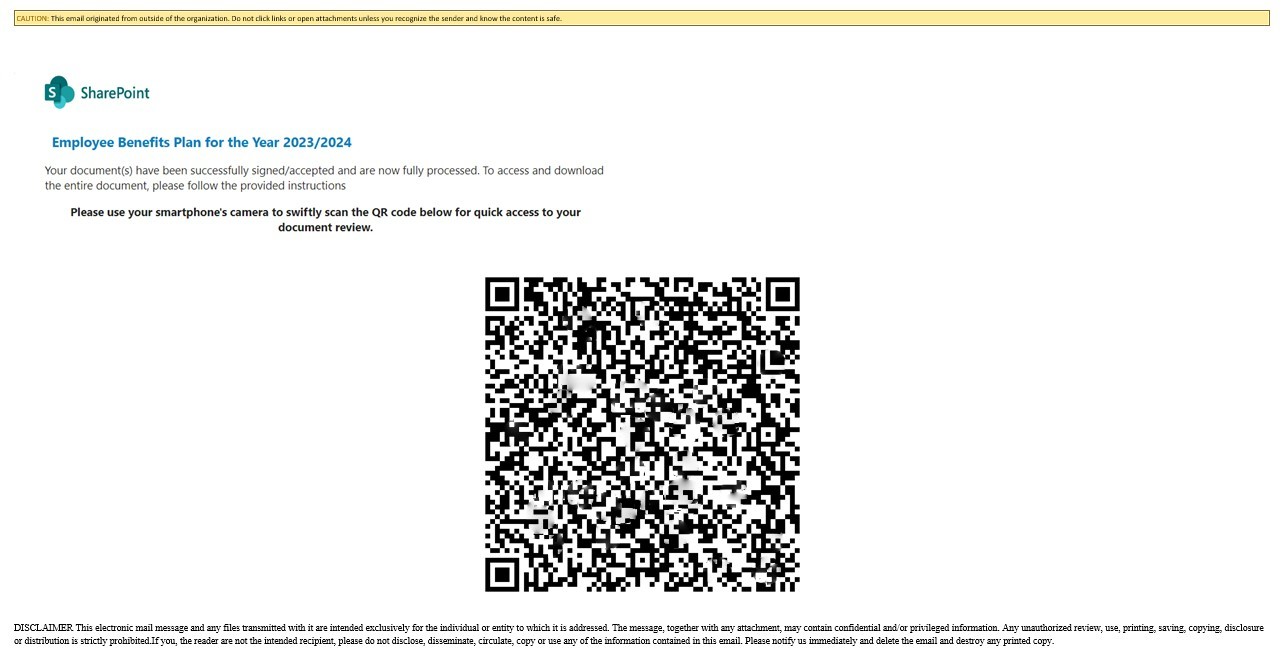
The “QR Code” Type Attack
Because most spam filtering will scan links and attachments in emails, attackers have tried to think ‘outside the box’ by creating a QR code which when scanned will take you to a fake Office 365 website. (The image had been obscured for security reasons)
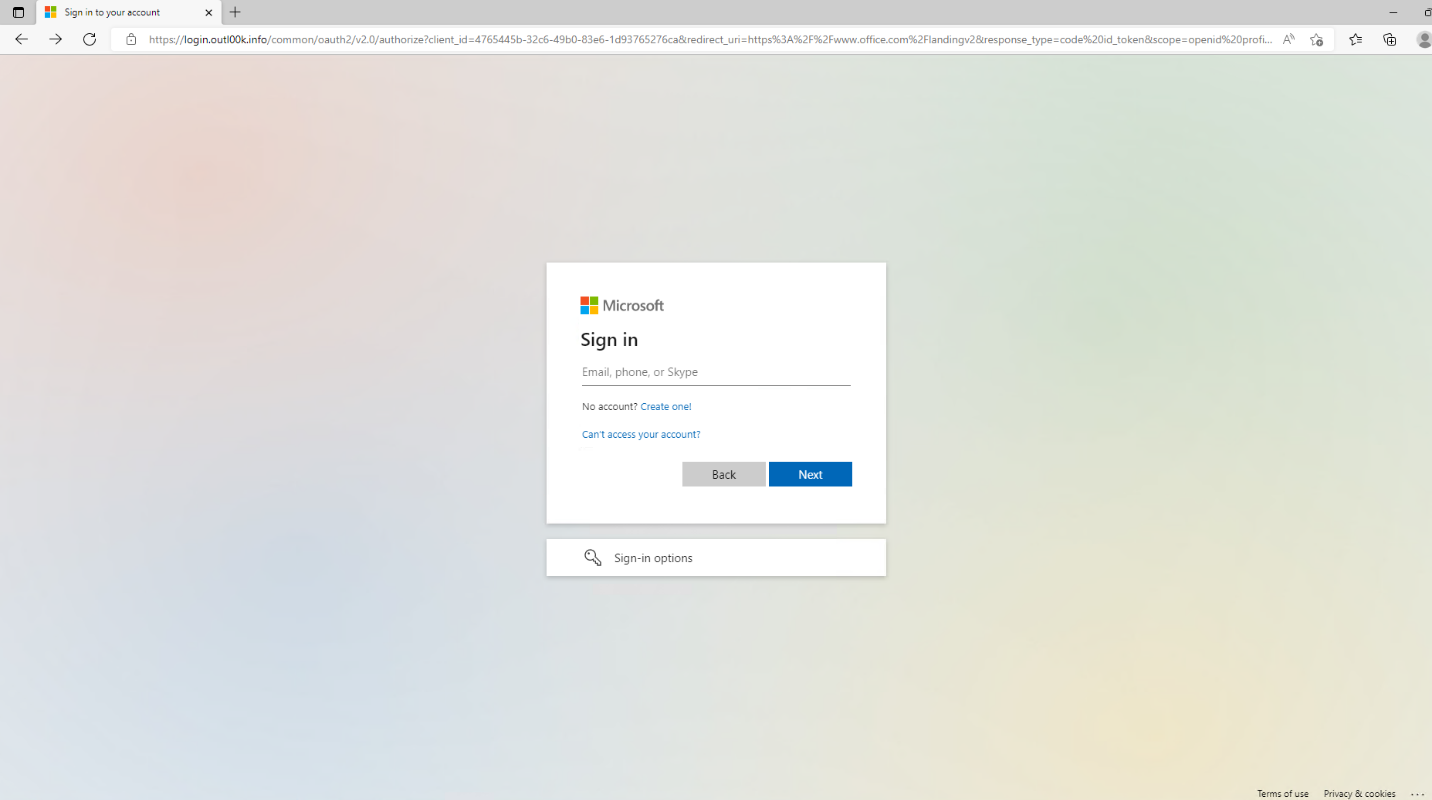
The “AITM Phishing” Type Attack
This is where you receive an email with a link that takes you to a fake Office365 website. This could be from a company or contact you deal with regularly, or a random email address. Remember, it’s always possible someone you deal with regularly has been breached and the attacker is leveraging your relationship with that person…abusing trust! See example image below, it looks exactly the same as the official Office365 website, but it is malicious!
NOTE: website address is not https://portal.office.com or https://login.microsoftonline.com
The MFA Bombing Attack
This is where an attacker keeps trying to log into your Office365 with the correct credentials obtained via DarkWeb or alike, until you approve the MFA prompt. They rely on the annoyance of you continually getting MFA prompts, until you reluctantly approve one, therefore letting them into your account. Office365 will not continually prompt you for MFA, so if this happens it’s likely someone is trying to get into your account. Again, if you are unsure or if there is anything out of the ordinary please contact us.
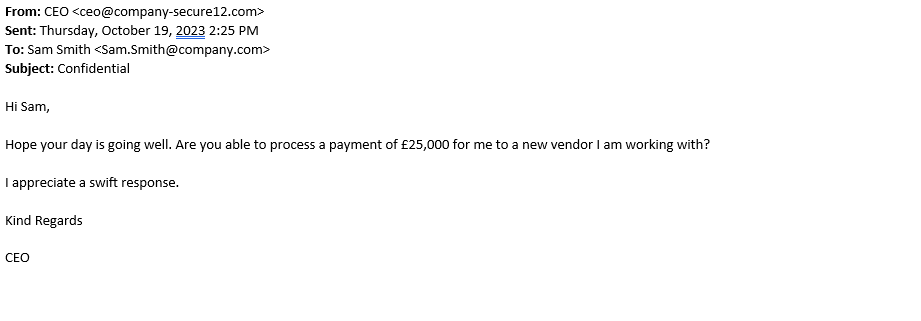
CEO Impersonation Phishing
Firstly, these types of attacks rely on pressure, speedy response, and trust. Typically, these are spear-phishing emails where an attacker impersonates the CEO or another Senior high-ranking employee within your organisation. These will generally try and trick you into transferring money owned by the attacker or sending HR confidential information for extortion. These can be sent to your work email, personal email, WhatsApp, SMS, or any other method of communication an attacker can find online.
Secondly, challenge yourself with what information you want to put online, if it’s online – Ask yourself, if it’s online, who can access it? Look at your LinkedIn or Facebook accounts, could an attacker answer any of your password recovery questions? Where did you grow up? Where did you go to school? What is your personal contact email or phone number? All of these pieces of information paint a picture, and most of the time these are a piece of the puzzle for an attacker.
Thirdly, when an email comes in always check the email address this has come from. Whilst the display name could be the actual CEO’s name, double check the actual email address. Anyone can setup a Hotmail or 3rd party email account in someone’s name. Would your CEO really email you direct to transfer money, or request thousands of pounds in iTunes vouchers? If you are ever unsure PAUSE, pick up the phone and call the person on the number you know is theirs and NOT by the number they have provided! Example below…
As with any security issue, if you have entered any credentials, or want to check the legitimacy of an email please contact Utilize immediately.
There are many things that you can do to protect your organisation and Utilize offer many services such as Office365 MFA, DarkWeb Scanning and simulated Phishing training. Contact us for more information or speak to your Account Director.
Remember proactive security is just the first step, don’t get caught out!
Contact Utilize


